Luminate and SentinelOne Team Up to Deliver Zero Trust Corporate Architecture
Luminate Security and SentinelOne announced a partnership yesterday that offers a joint solution for Zero Trust Architecture. The joint solution combines technologies from both companies to ensure that only authenticated users with secure endpoints can access corporate applications in hybrid or multi-cloud environments.
The news provides yet another example of how enterprises can benefit from solutions that provide robust security while they transition to cloud and hybrid models and grant workers a far greater degree of mobility than every before. To achieve these goals, it is necessary to secure endpoints but also defend against unauthorized network access and “lateral movements” inside of networks.
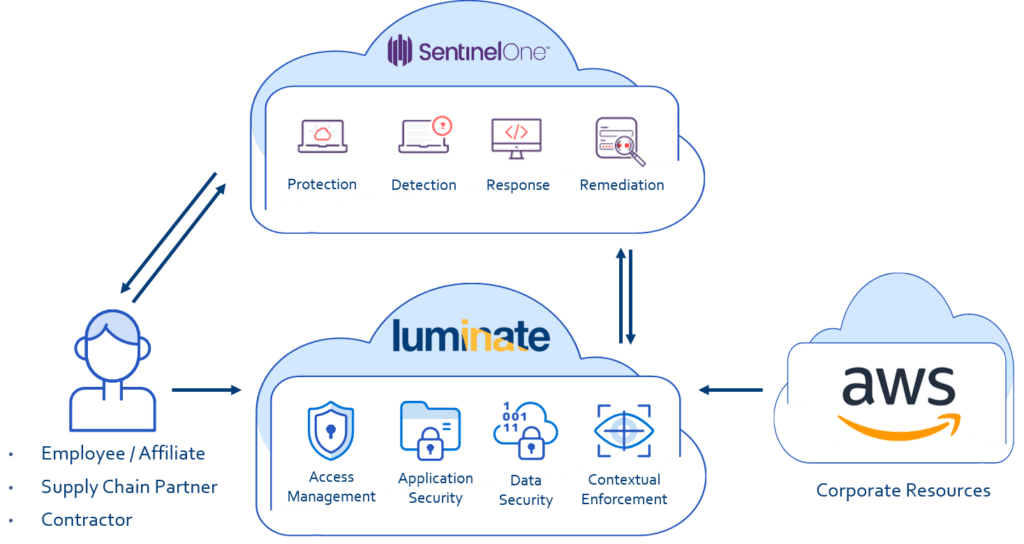
Each company brings unique capabilities to the joint solution. Luminate is a software-as-a-service security platform that manages access to corporate resources from any device anywhere in the world. The Luminate solution is based on Software Defined Perimeter principles. Luminate gives users one-time access to a requested application while cloaking all other corporate resources. Users are not granted access to the entire network. This prevents any lateral movements to other network resources and eliminates the risk of network-based attacks.
SentinelOne is in the business of autonomous endpoint protection. Through a single agent, the company’s S1 platform prevents, detects and responds to attacks across all major vectors. It is designed for ease of use. Through AI, it can automatically eliminate threats in real time for both on premise and cloud environments. The only solution provides full visibility across networks directly from the endpoint.
“Enterprises today are facing a truly disintegrating perimeter,” said Raj Rajamani, VP of Product Management, SentinelOne. “The new perimeter, such as it is, requires a new approach to security.”
Reference architecture for the joint solution from Luminate and SentinelOne. How it works: 1) Complete isolation and cloaking; 2) Authenticate user and verify device security posture; 3) Layer-reverse connection; 4) visibility and security
Rajamani offered an example of how Zero Trust and endpoint security come together to defend a typical modern enterprise. “Imagine you have source code on GitHub,” he said. “You might allow a remote user to access that source code from a mobile device. However, if that device was hacked, you could be exposing your intellectual property to malicious actors. With our solution, you can specific which digital asset the user is allowed to access. He or she will get nothing more. At the same time, we can protect the endpoint itself.”
The timing of the joint solution is auspicious. Over 8o percent of enterprises worldwide have a multi-cloud strategy with most organizations leveraging as many as five clouds. Corporate applications are moving to the cloud with enterprise environments becoming hybrid and distributed. As a result, traditional network perimeter security techniques, such as VPNs and DMZs, no longer support current business needs and protect the organizations’ assets. To eliminate exposure of the network, security architecture must shift from the network-level to the use of applications with access based on the user’s identity and device.
“Organizations that move to cloud and hybrid environments must ensure that only authenticated users with secure endpoints can access corporate applications and resources,” said Eldad Livni, Chief Product Officer at Luminate. “The integration of Luminate and SentinelOne creates a model of Zero Trust application access, automatically validating the user identity and device posture before providing access to corporate resources in the cloud. With Luminate’s continuous application access governance, joint customers gain visibility into user actions and application usage, while ensuring continuous security to prevent malicious usage of corporate assets.”
The Zero Trust access solution formed by the integration of Luminate and SentinelOne ensures business continuity and security in the cloud. SentinelOne’s autonomous endpoint protection secures devices against the latest attacks. Combined with the power of Luminate Secure Access Cloud™, customers can make sure that only authenticated users from secure devices can access corporate IT resources rather than counting on validation of “trusted employees” as the security factor. Relying on the user authentication throughout each session provides an essential level of continuous protection to corporate applications, and prevents attackers from compromising a device and posing as a trusted employee to gain access to sensitive information.
“In the Zero Trust model, the endpoint becomes critical as it is the closest point to the user where the enterprise has full control,” said Daniel Bernard, VP Business Development at SentinelOne. “With this integration, SentinelOne and Luminate ensure that corporate employees can work securely. The joint solution enforces endpoint security by blocking the access of end-points that are not defined as safe by SentinelOne, while dynamically monitoring and governing application usage and user activity by Luminate.”
