IIOT Security Challenge: Building a Policy Enforcement Architecture
Business and government leaders are only now starting to come to grips with the cyber vulnerabilities of the Internet of Things (IoT). Industry, in particular, with its Industrial Internet of Things (IIoT), faces quite serious risks. These include nuisances and fraud like crypto mining but also espionage, intellectual property theft and even cyber terror.
The IIoT comprises an extended array of industrial facilities and public utilities. Run on SCADA systems, these include wastewater treatment plants, dams, chemical plants, nuclear plants, electrical power grid facilities, manufacturing plants, railways and so forth. When facilities like this get breached, there is potential for mass mayhem and death.
Beyond Any Single Technology
Addressing the threats to the IIoT, and by extension, anyone who is affected by the IIoT (and that would be basically, everyone) takes more than just a single technology solution. It’s a matter of architecture, as Ilan Barda, CEO of Radiflow, explained. “Securing an IIoT environment requires knitting together a number of disparate technologies and their respective management teams,” he said. Radiflow makes Intrusion Detection Systems (IDSs) especially for the IIoT. “There’s been a traditional separation between IT and OT. Now, we have to close that gap.”
When facilities like this get breached, there is potential for mass mayhem and death.
OT, or Operational Technology, was historically separate from IT. There were (and are) many good reasons for this

Ilan Barda, CEO of Radiflow
division, including significant differences in the technology itself as well as divergent work cultures. “OT is about operations, about making things, providing services and making money,” Barda noted. “IT is about connecting everyone and delivering technology service quality.”
An Architectural Approach to IIoT Security
In order for an IIoT to be secure, it must embody a fundamental architecture designed for security policy enforcement. In the Radiflow approach, shown in the graphic depicting an IDS for a SCADA based water system, the industrial firewall operates at each stage of the water management cycle. It can detect threats and anomalies across the water system’s operational processes.
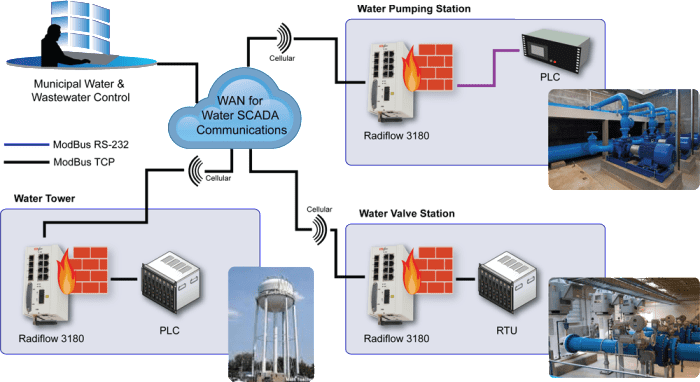
This is a good start, but the placement and connection of industrial firewalls is not adequate on its own to provide robust IIoT security. To work, the architecture must include connectivity with other IT and OT control system as well as security incident response systems. The SOC has to be able to integrate a Radiflow IDS, or equivalent, into its alerting and incident response workflows.
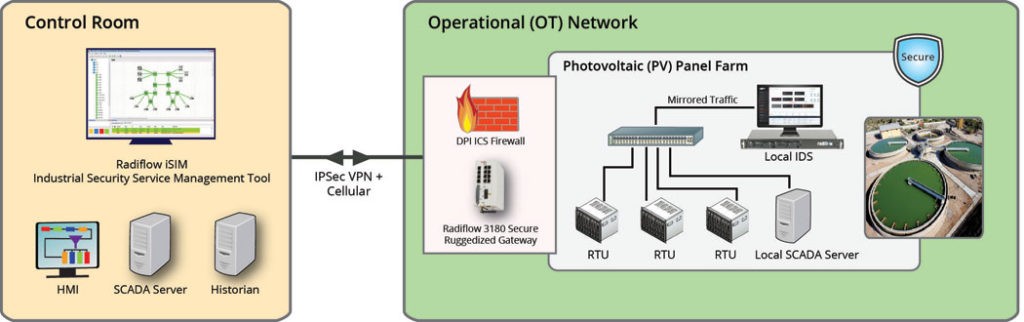
Architected in this way, the IIoT security solution becomes a pervasive point of policy enforcement. An organization might establish a security policy of intrusion detection at the perimeter level of IIoT devices, but it will only work if the architecture supports its enforcement. Radiflow enables such an IIoT policy enforcement architecture to exist.
