Staying Ahead of Evolving Mobile Threats
Corporate computing is going mobile, with mobile corporate internet usage surpassing desktops in 2016. Now, mobile and tablets account for a full 57% of corporate internet use. With this trend, though, there’s been a commensurate increase in cybercrime targeting mobile devices.
Why wouldn’t there be? Hackers want to be where the action is. The problem for hackers is that mobile devices typically have stronger basic security than their desktop peers. Between mobile device manufacturers and telecom carriers, mobile apps tend to get more vetting than traditional software. Operating systems are more tightly controlled. Sandboxing is more common as well, making data leakage less likely.

Michael Covington, VP of Product Strategy at Wandera
The attackers have improvised in response. Mobile phishing, for example, has become far more sophisticated in recent years. Phishing URLs have adapted to mobile browsers. Also, according to Michael Covington, VP of Product Strategy at Wandera, the mobile device security company, we’re experiencing a rise in “malvertising.”
The practice, which sounds like something that should have been cut out of the script of Mad Men, involves placing phishing links in mobile ads that get served through bogus ad networks. “It’s pretty crafty, you have to admit,” Covington remarked. “You might be using an app on your phone that’s totally legitimate, but the ad running at the bottom of the screen is phishing bait.”
Covington further outlined why mobile use is becoming riskier as hackers reinvent themselves for this age of mobile internet. Citing research from Gartner, IDC and CIO as well as Wandera itself, he shared a few startling facts: Over 50% of corporate data usage is not business critical; One in seven employees accesses adult, gambling or extreme sites weekly on mobile devices; 72% of employees use unauthorized “Shadow IT” services like public cloud-based file sharing services; 25% of all business have devices that are being cryptojacked; One third of all malware will be mobile by 2019; and, one in 25 mainstream apps leak sensitive credentials.
Ouch! Seriously, how are you supposed to play online poker on your corporate-issued mobile device if it’s being used for cryptojacking? That doesn’t seem fair.
What’s clear is that corporate mobile devices now present a far broader attack surface area than ever before. Risk mitigation processes must keep pace with the rapid evolution of the threat landscape. This is the work Wandera has undertaken.
How are you supposed to play online poker on your corporate-issued mobile device if it’s being used for cryptojacking? That doesn’t seem fair.
Wandera belongs to a new generation of cyber security companies that are transcending the static modes of protection that have dominated the field for years. They seem to understand that the threat actors are not standing still, so the defender can never rest, either. Theirs is a dynamic, wide-ranging set of countermeasures.
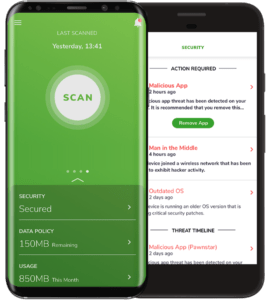
The Wandera app
Structurally, Wandera is pretty simple. It’s an app that tracks mobile device usage and system characteristics. The app connects to a mobile first gateway that interfaces with a real-time threat intelligence and reporting engine. There is no VPN, which can introduce performance lags and drain batteries. Beyond this simple architecture, however, lies a rich threat detection and response capability.
The app looks for suspicious behaviors, like excessive CPU usage. It also flags known malware, potentially untrustworthy access points or data leakage. For example, if the device is sending out personally identifying information (PII) without encryption, Wandera will issue an alert. This event could signal an attack or use of insecure mobile site. Both expose the device (and the device issuing organization) to risk.
It never stops. This is the new world of cyber security. Every second, as the threat intelligence database grows larger and smarter, the app continues its vigil. It’s a continuous process.
Wandera is also approaching mobile security from a holistic perspective. For instance, as companies shift to an all-mobile strategy and provision employees with a single device for mobile and virtual desktop use, they need a security solution that works across all use cases. This is the Samsung strategy, where the DEX solution enables a worker to move around a corporate campus with a Samsung phone that plugs into docking stations and transforms into a desktop experience.
It never stops. This is the new world of cyber security. Every second, as the threat intelligence database grows larger and smarter, the app continues its vigil. It’s a continuous process.
The security challenge in this case, however, is to ensure that all communications between the device and corporate network are secure. “There’s a potential gap in security with phones acting as virtual PC,” Covington noted. “If you’re relying on cellular connections for backhaul to the corporate network, you’re making yourself vulnerable.” Wandera tracks such connections along with everything else. They partner with the major players in the space, including Citrix, Samsung, and IBM.
These are early days for mobile security. The innovations we’re seeing in the market are encouraging, though. As mobile device use becomes a universal aspect of corporate life, we’re going to need all the help we can get.
