RSA 2018 Profile: XM Cyber
If Dr. Seuss had been a cybersecurity professional, he might have written a book called “One phish two phish red phish blue phish.” Today, the XM Cyber team will have to write this story. The company’s platform conducts what amounts to a continuous “red team” penetration testing exercise on a network. It then adds a continuous series of “blue team” recommendations to remediate network vulnerabilities. The red team and blue teams combine in XM Cyber, forming what the company calls a “purple machine” for security.

Noam Erez, Co-Founder and CEO of XM Cyber
Based on techniques developed during the management team’s long careers in the Israeli military and intelligence organizations, the XM Cyber platform can simulate, in real time, how a customer’s network can be compromised. It demonstrates how an actual vulnerability in a real device on the network, e.g. a server, can be taken over—and then spread the attack across the network. Visually, the display shows attack vectors in red and policy remediation suggestions in blue.
“What a lot of people don’t realize is that some of the worst attacks are actually quite simple in nature,” said Noam Erez, CEO and Co-Founder of XM Cyber. “However, a simple attack, like taking over a server with its user’s credentials still cached in memory, can lead to devastating business impacts. If you’re not watching your network all the time, you’re guaranteed to miss even a relatively primitive but deadly attack.”
The XM Cyber solution continuously exposes all attack vectors, above and below the surface, from breach point to any organizational critical asset. A continuous loop of automated red teaming is completed by ongoing and prioritized actionable remediation of organizations’ security gaps. “Our platform operates as an automated purple team, so to speak,” Erez added. “It fluidly combines red team and blue team processes to ensure that organizations are always one step ahead of the hacker.”
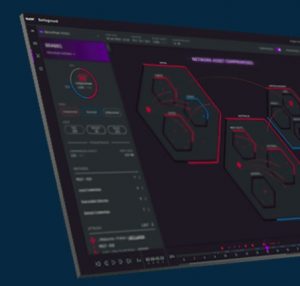
XM Cyber platform’s visualization of a network attack in real time.
Cyber Policy Take
XM Cyber offers a solution to the degradation of controls over time, one of the most serious challenges facing cyber security managers. An organization could define a security policy for network security and then proceed to implement a strong network defense countermeasure. As of January 1, it’s working, but by March, holes have opened up in it—and the SecOps team might not know. The control is deficient, but it’s a stealth vulnerability.
The policy has been defined but not enforced. It’s essentially meaningless. Hackers can find the hole. With the kind of continuous attack simulation available through XM Cyber, there’s now a way to test the control repeatedly and have confidence that the policy is being enforced as it was intended.
