Research: top countries by exposed credentials and databases online
Nearly 10,000 exposed databases with 10 billion credentials were found online
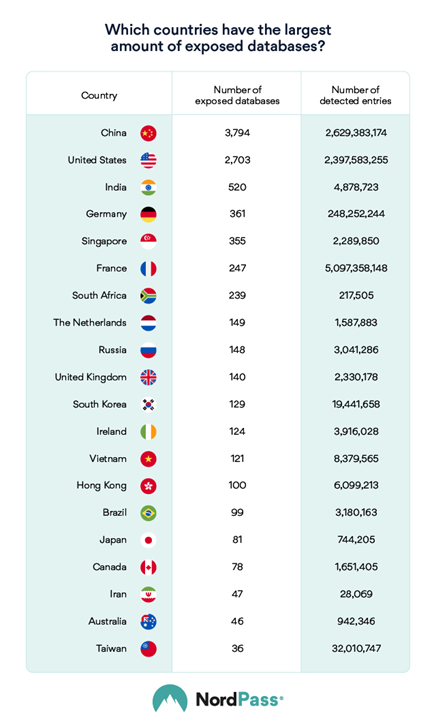
5 August 2020. China is the ultimate leader when it comes to unsecured databases and free-for-all credentials, research has found. The country has 3,794 exposed databases with 2,629,383,174 credentials.
Second on the list is the United States, with nearly 3,000 unsecured databases and almost 2.3 billion entries made available online.
India was third, with 520 unsecured databases and more than 4 million entries.
In total, researchers found 9,517 unsecured databases containing 10,463,315,645 entries with such data as emails, passwords, and phone numbers.
Here is the full list of countries and the amount of exposed databases along with available credentials:
| Country | How many databases have been breached? | Number of detected entries |
| China | 3,794 | 2,629,383,174 |
| United States | 2,703 | 2,397,583,255 |
| India | 520 | 4,878,723 |
| Germany | 361 | 248,252,244 |
| Singapore | 355 | 2,289,850 |
| France | 247 | 5,097,358,148 |
| South Africa | 239 | 217,505 |
| The Netherlands | 149 | 1,587,883 |
| Russia | 148 | 3,041,286 |
| United Kingdom | 140 | 2,330,178 |
| South Korea | 129 | 19,441,658 |
| Ireland | 124 | 3,916,028 |
| Vietnam | 121 | 8,379,565 |
| Hong Kong | 100 | 6,099,213 |
| Brazil | 99 | 3,180,163 |
| Japan | 81 | 744,205 |
| Canada | 78 | 1,651,405 |
| Iran | 47 | 28,069 |
| Australia | 46 | 942,346 |
| Taiwan | 36 | 32,010,747 |
Sensitive vs testing data
While some of this data might be useless and only used for testing, much of it could be damaging if exposed. Some of the largest data leaks of last year resulted from exposed databases. For example, millions of Facebook records were exposed on a public Amazon server. In another incident, an unsecured database exposed information of 80 million US households. The data included victims’ addresses, income, and marital status. A rehabilitation clinic in the US also suffered from a data leak, over which nearly 150,000 patients had their personal information exposed. The most worrying part is that this data was not leaked by a persevering hacker — it was simply sitting there in a public database.
Low-skilled job
While the idea of searching for exposed databases may seem complex, the process itself is quite straightforward. Search engines like Censys or Shodan scan the web constantly and let anyone view open databases in just a few clicks. If the database managers used the default logins, getting into one would be a piece of cake.
“In fact, with proper equipment, you could easily scan the whole internet on your own in just 40 minutes,” says Chad Hammond, security expert at NordPass.
Attacks against unsecured databases
Recently, unsecured databases have been hit by a “Meow” attack, which wiped clean thousands of them. “These kinds of attacks are very frequent. Usually, the attacker asks for ransom. This attack seems to be different only because the hackers deleted the data instead of asking for ransom,” says Chad Hammond, security expert at NordPass.
The NordPass security expert estimates that 39% of all databases have already been hit by one of these ransomware attacks.
“The Meow attack against unsecured databases should only reinforce the need for proper #data security. And while some of the affected databases only contained testing data, the Meow attack targeted some high-level victims, among which was one of the biggest payment platforms in Africa,” says Chad Hammond.
The essentials of database security
Data security and protection should be a top priority. “Every company, entity, or developer should make sure they never leave any database exposed, as this is obviously a huge threat to user data,” says Chad Hammond.
When asked to highlight the main points of database security, the expert emphasized:
“Proper protection should include data encryption at rest, wire (in motion) data encryption, identity management, and vulnerability management.
Data can be exposed to risks both in transit and at rest and therefore requires protection in both states. While there are several different approaches, encryption plays a major role in data protection and is a popular tool for securing data both in transit and at rest.
Nevertheless, all data should be encrypted using trusted and robust algorithms instead of custom or random methods. It’s also important to select appropriate key lengths to protect your system from attacks.
Identity management is another important step and should be used to ensure that only the relevant people in an enterprise have access to technological resources.
Finally, every company should have a local security team responsible for vulnerability management and able to detect any vulnerabilities early on,” says Chad Hammond.
As for the users, the security expert yet again draws attention to the importance of a strong password. “The fact that we have more than 10 billion passwords up for grabs should only encourage people to think of strong, lengthy passwords. If your password is “12345”, no firewall in the world will protect your data. Your password shouldn’t be a dictionary word either — an average person uses only about 20,000-30,000 words, so chances are that all of them are already among those 10 billion,” says the NordPass security expert.
Methodology: NordPass partnered up with a white hat hacker, who scanned elasticsearch and mongoDB libraries, looking for exposed, unprotected databases. Once found, he logged into those public databases and checked what kind of data could be found there. The white hat hacker has shared with NordPass how many exposed databases and entries he had found. The hacker requested to stay anonymous. Time frame: June 2019 to June 2020.
ABOUT NORDPASS
NordPass is a new-generation password manager shaped with cutting-edge technology, zero-knowledge encryption, simplicity, and intuitive design in mind. It securely stores and organizes passwords by keeping them in one convenient place. NordPass was created by the cybersecurity experts behind NordVPN — one of the most advanced VPN service providers in the world. For more information: nordpass.com.
Infographic: