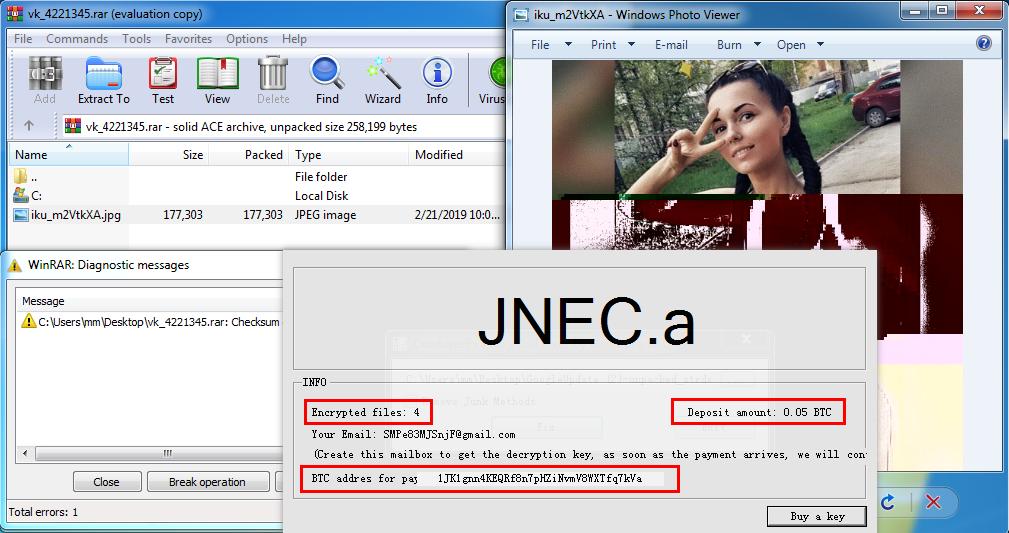
News Insights: JNEC.a ransomware targeting users via WinRAR AC
In response to news of JNEC.a ransomware targeting users via the WinRAR ACE vuln (#CVE-2018-20250), an expert with STEALTHbits offers perspective.
According to Adam Laub, SVP Product Management, STEALTHbits Technologies, “While every ransomware variant seems to have its own unique twist, their goal is almost always the same – encrypt as many files as possible and count on the desperation of victims needing to reclaim their property in the face of losing it all.
While the user at home and the user within an enterprise are essentially compromised in the same way, the user in the enterprise poses risk to far more users and their data, provided the ransomware is intelligent enough to spread.
At a minimum, patching known vulnerabilities can help mitigate the risk of further infiltration of a corporation’s network. But ultimately, the reduction of data access and permissions to only the levels needed for each user across file infrastructure is one of the best mitigation options to ensure the impact of any successful ransomware attack is limited.
Ransomware of any type relies on at least the permission to modify data. However, most users only need to be able to read the data they have access to. Unfortunately, users often have much higher levels of permission to data than they need, making most ransomware attacks exponentially more successful than they ought to be.