New API Research Shows 62% Growth in ATOs Targeting Login APIs
APIs are the Developer Tool of Choice and 1 Target for Malicious Use
Today, everything is an app. A Tesla isn’t really a car – it’s a four-wheeled app. Every one of the 142B+ device app downloads including your money management or a favorite shopping or fitness app are all built on application programming interfaces (APIs). The user interface that is designed to deliver an engaging user experience is supported by APIs connecting back to compute resources located elsewhere – be it the cloud, the data center, or both.
Validating that APIs are the development tool of choice, the most recent Cequence Security API Usage and Threat Report found that 14.4 billion or 70% of the 21.#1 billion application requests analyzed were #API-based. Designed for machine-to-machine interaction, APIs provide developers with great flexibility, allowing them to create complex functionality that executes the entire transaction including payload. Usage patterns validating these findings include increased usage of GraphQL for development and APIs referencing health monitoring services, OpenAPI specifications, and sensitive data patterns.
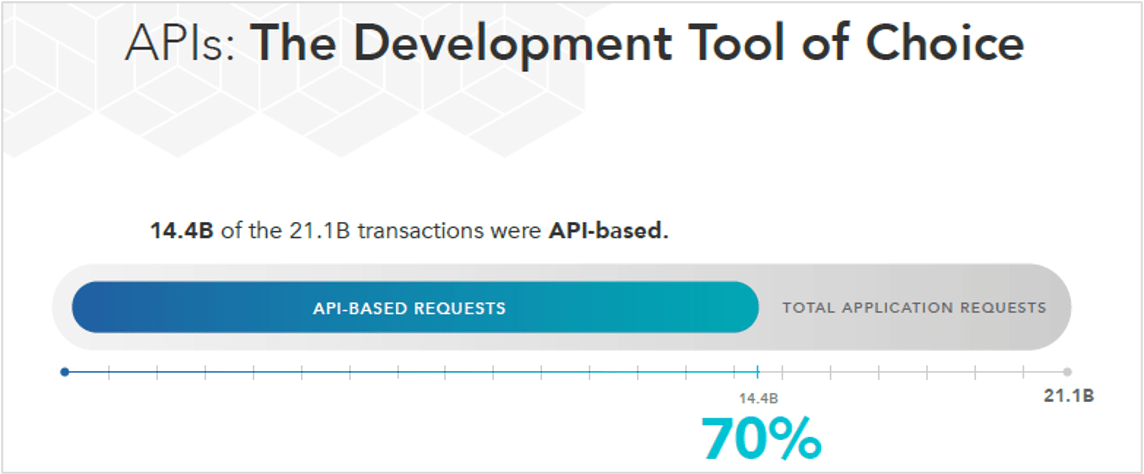
That same power and flexibility found in APIs are also leveraged by attackers, who use their developer skills for malicious purposes. The analysis confirms that APIs are the preferred target for malicious use with 80% or 1.8 billion blocked attacks found to be API-based. APIs simplify the execution of sophisticated, hard to prevent automated attacks and business logic abuse, highlighted by an increase in ATOs against login APIs and a surge in content scraping against APIs.

Login APIs Targeted by 62% Increase in ATOs
During the June to December 2021 analysis period, the data reflects a 95% increase in the use of APIs to facilitate account logins and registrations. That increase in activity is mirrored by a 62% increase in account takeovers (ATOs), known to be one of the most common automated attacks and often the precursor to different types of fraud. As an example, gift card fraud was increasingly common during 2021 as a whole, driven in large part by the pandemic. Successful ATOs lead to card or points theft, fraudulent purchases, or resold for profit, impacting businesses with lost revenue, disgruntled and frustrated customers, and increased infrastructure costs.
Wreaking a greater financial impact on organizations and users, ATOs are the first step in loan fraud. In 2021, attackers targeted APIs supporting financial membership sign-up program offerings that included automatic qualification for small dollar figure loans. Using a combination of APIs and manual efforts, attackers launched large-scale ATO attacks, and if successful, were able to then apply for a pre-qualified loan resulting in financial fraud.
Content Scraping Against APIs Skyrockets 178%
Content scraping often viewed as benign but in reality, can be difficult to prevent and can dramatically impact an organization’s bottom line, saw a massive uptick of 178%. The term content scraping is often equated to web or HTML-based content, however, when analyzing the most common type of content stolen – pricing, part numbers, product descriptions – the dramatic uptick makes perfect sense.

APIs are used to call inventory and pricing databases thereby facilitating the use of automation to quickly and easily steal the desired content. The business impact of content scraping includes loss of intellectual property, increased competitive pressure on sales margins, and compute resource cost overruns.
APIs at Risk: System Health, Sensitive Data, and Internal API Exposure
Looking at the data from a developer-centric perspective, the analysis shows growth in the use of new tools like GraphQL and the adoption of OpenAPI specifications, both of which can accelerate the delivery of more secure and consistently coded APIs. On the flip side, the analysis showed dramatic increases in APIs that use or can expose too much data, introducing potential security risks.
- OpenAPI/Swagger and GraphQL on the Rise. APIs that referenced OpenAPI or Swagger specifications jumped 352%, signaling an uptick in adoption that can lead to higher quality and more secure APIs. However, when care is not taken to control public access to the specifications, they can provide a blueprint for an API attack. GraphQL, a new, rapidly growing development technology that offers speed and flexibility saw usage increase 133% over the six-month period. Too often, new technology adopted (too) quickly can introduce security risks.
- APIs and Data Exposure Risks Skyrocket. Health monitoring APIs, used much like a blood test to uncover system problems, skyrocketed 941%. When coded without considering the security best practice of using minimal information, attackers can use the system information for malicious purposes. The use of APIs that include sensitive data such as payment or personally identifiable information jumped 87%, emphasizing the continued need for strong security and privacy during API development. Public-facing APIs linked to internal or non-production applications grew by 46%, reminding organizations that they should adopt the position of treating all APIs as if they are internal to prevent inadvertent API exposure.
3 Steps to Comprehensive API Security
Comprehensive API security requires a prevention-first approach that combines complete API visibility, runtime risk assessment, and remediation with native, inline attack prevention.
- Step 1: API Discovery and Inventory Tracking: You cannot protect what you cannot see. Integration with any element of your API management infrastructure using either an inline or out-of-band data collection ensures all APIs are found, tracked, categorized, and assigned a respective owner.
- Step 2: API Risk Assessment and Remediation: Acting as a final security check, using predefined or custom risk assessment rules helps uncover and remediate APIs with weak authentication, exposing sensitive data, using verbose error messages, or out of conformance with published specifications.
Step 3: Native, Inline Protection from Attacks and Vulnerability Exploits: Even a perfectly coded API can be attacked, strengthening the need to actively analyze and prevent attacks in real-time, using predefined, customizable policies with response options that include log, block, rate limit, geo-fence, header injection, or deception configured per app or API.

