Kudos to Upstream for Publishing Research on Automotive Cyber Vulnerabilities
I am a big admirer of thorough, thoughtful research into serious subjects that do not get enough attention in the mainstream. Reading the “Upstream Security Global Automotive Cybersecurity Report” for 2019, you can immediately see that a great deal of work and outside-the-box thinking went into it. So, kudos to Upstream for taking the initiative in this important area of cybersecurity.

Oded Yarkoni, VP of Marketing at Upstream
The report, available online or in a handsome printed edition, adds structure and quantitative metrics to a previously abstract problem: cyber risks in connected cars. For one thing, the report offers a systematic way of looking at cyber risks in the automotive industry. It breaks down attack vectors, revealing, for example, that back end servers (e.g. telemetry data servers or remote access servers) account for 21% of cyber attacks on connected cars. That is the most prevalent form of attack, followed by keyless entry attacks (18%), OBD port attacks (10%) and so forth.
Upstream also calculates the cost of automotive cyberattacks. They did this by imputing the costs of recalls, suggesting that an attack would cost an automaker up to $1.1 billion. This is probably a conservative figure, given the costs of litigation, personal injury, violations of privacy laws and so forth. Based on Juniper Research’s prediction of 775,000,000 connected vehicles on the road by 2023, Upstream forecasts the automotive industry will be facing $24 billion in risk exposure due to cyber threats. As they say in Detroit, that’s a lot of cabbage.
Based on Juniper Research’s prediction of 775,000,000 connected vehicles on the road by 2023, Upstream forecasts the automotive industry will be facing $24 billion in risk exposure due to cyber threats. As they say in Detroit, that’s a lot of cabbage.
I won’t drop any more spoilers on the report. It’s worth a read, if for no other reason than it showcases the kind of massive, stealth risk exposure that modern societies are facing in category after category. It highlights an area of risk that is underappreciated, both by the public and in government: the cyber-physical threat.

A hacked car is a not just a source of data breach. It’s a potentially deadly weapon. It can kill people, including the passengers and anyone standing in the way. It can disrupt economies by bringing transportation to a halt. Anyone tasked with protecting a country from cyber attack should be paying close attention to reports of this kind.
A hacked car is a not just a source of data breach. It’s a potentially deadly weapon.
What can be done about these risks? This is the problem that companies like Upstream are trying to solve. Their approaches vary, though Upstream’s agentless approach seems promising. Their premise is that the car itself is not the place to manage automotive cybersecurity. The connected car is a labyrinth of interdependent systems built by many different sub-contractors.
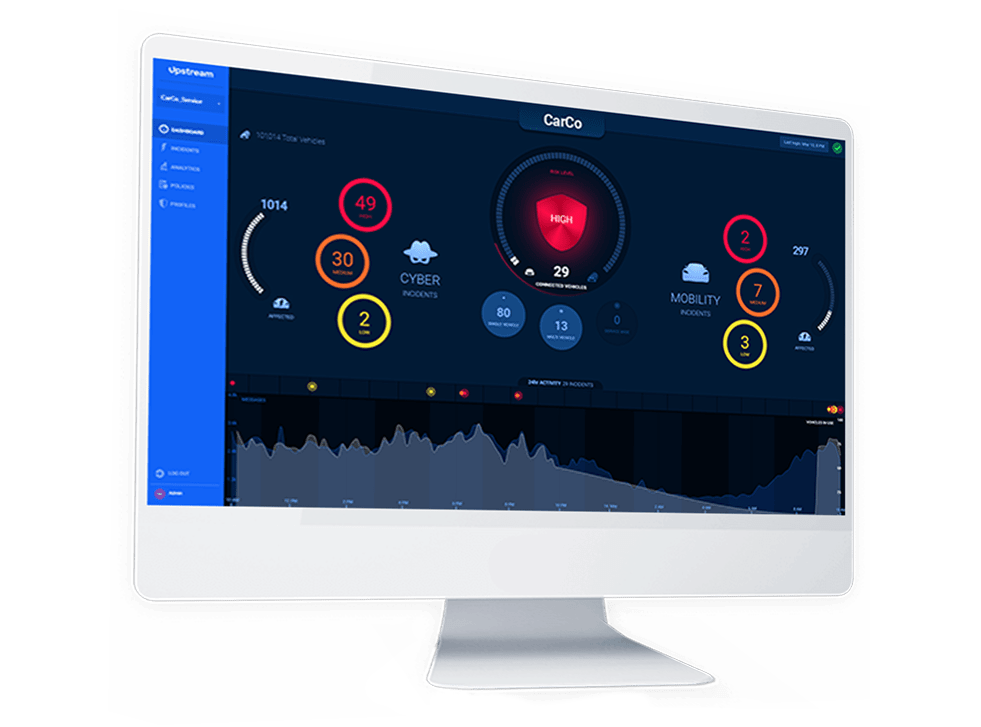
Upstream’s dashboard
“Even if you had access to the car, which itself is a dubious assumption, you would never realistically be able to mitigate risk in each sub-system,” explained Oded Yarkoni, VP Marketing at Upstream. “From there, it would be an endless game of catchup.”
“We’re not plugging anything into the car, so no one worries that we could disrupt their systems.”
Instead, Upstream works at the level of the vehicular data streams. This is a zero-impact, zero-risk approach. “We’re not plugging anything into the car, so no one worries that we could disrupt their systems,” Yarkoni added. Connected cars create more than one stream of data as they operate. The automaker may get data about engine performance and other telemetric information. The fleet manager gets location and speed data, and so forth. Upstream parses these streams, normalizes and correlates the data, looking for patterns. Their solution “learns” what is normal for a given fleet of vehicles in order to spot suspicious anomalies.
One advantage of this approach is the ability to identify fleet-wide attacks early in the kill chain. “If one car switches lanes without the driver intending it, that’s a single-car incident, with many different explanations,” Yarkoni explained. “If five hundred cars switch lanes at the same time, that’s a cyberattack, and we’ll know about it in seconds.”
Photo by https://www.pexels.com/@pixabay

![[Latest] Cloud Ran World Market Analysis | Application Grows in Network Services and Custom Services, 2022-2032](https://journalofcyberpolicy.com/wp-content/themes/first-mag-pro/img/noprew-related.jpg)