Illusive Networks Announces Breakthrough in Attack Surface Reduction
Illusive Networks, which specializes in deception-based cybersecurity solutions, has announced Attack Surface Manager (ASM), the first automated solution to continually reduce the attack surface, and proactively lower the likelihood of targeted cyberattack success. Illusive ASM discovers hidden elements throughout the network that enable lateral movement and otherwise facilitate advanced attacks.
In today’s fast-changing business environments, it is difficult for security teams to identify and control credentials and other sensitive data elements that proliferate during normal day to day operations. ASM automatically identifies these risks, revealing policy violations, and enabling security professionals to proactively deprive attackers of the keys they need to reach critical assets.
“For years, organizations have felt at the mercy of sophisticated attackers who maneuver their network undetected for months,” said Ofer Israeli, CEO, Illusive Networks. “By removing the very elements attackers need to progress, ASM stops the attack before it creates a business crisis. This significant new release continues our progress in addressing the complete advanced attack lifecycle.”
“Nearly every security breach that I’ve investigated involved the theft and abuse of credentials,” says Charles Carmakal, vice president of cyber incident response firm Mandiant. “ASM enables organizations to identify and decrease the exposure of credentials, reducing the ability for attackers to move laterally once in an environment.”
In a recent CyberEdge survey, only 38% of respondents stated they were confident in their ability to avoid a successful cyberattack in the coming twelve months. ASM was developed in response to customer requirements to eliminate standing threats missed by traditional cyber defense offerings, and represents continued progress toward Illusive’s vision of applying deception-based technology against all stages of advanced cyber-attacks, including prevention, detection, response, and remediation.
The Role of Deception Solutions
Deception solutions will play a greater role in the future of enterprise threat defense,” according to Gartner. Detection is often a prerequisite for higher-quality deceptions. However, organizations are beginning to use deceit to actively thwart or isolate malware botnets, threat actors and suspicious connections.1
“While some organizations may need large-scale analytics solutions or advanced threat hunting teams,” Israeli continued. “These investments take time to bear fruit. We provide an extremely lightweight, nimble, and easy to deploy solution that automatically adapts to changes in the environment, and immediately enhances an organization’s ability to avoid the heavy toll targeted attacks can take.”
Preemptively Manage and Reduce Attack Risk
Organization using ASM preemptively manage and reduce attack risk through:
- Continuous minimization of the attack surface, even when user populations and systems are rapidly changing
- Unprecedented visibility to their access footprint and credential-related policy violations that facilitate attacker mobility
- Efficient and scalable credential management of credentials through intelligent automation
- The ability to prioritize remediation by understanding the risk and criticality of each violation
- Early detection of advanced attackers by reducing attack vectors in the environment, decreasing real credentials, and increasing the odds of detection
- Rapid correction of policy violations by both automated and manually-driven methods
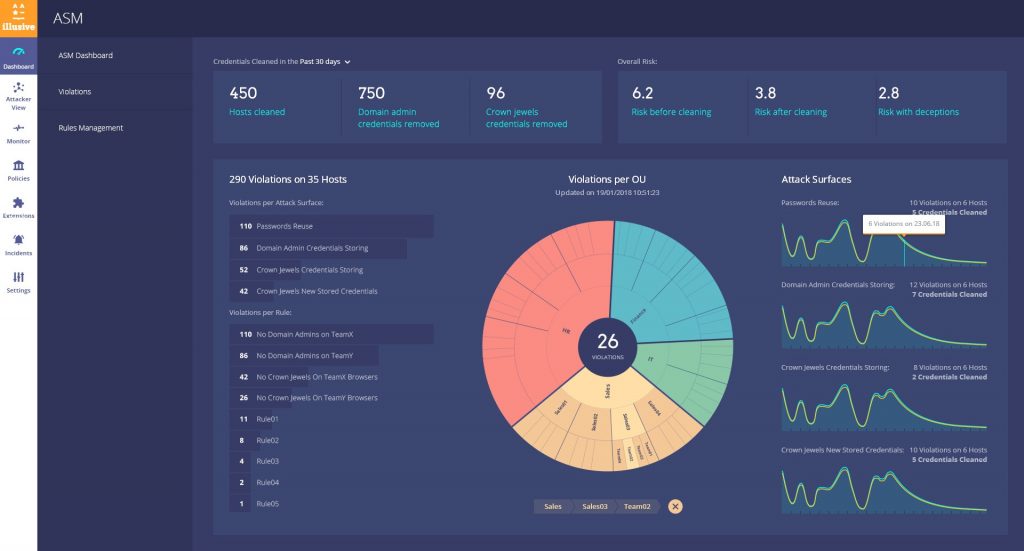
Screen shot of Illusive ASM.
ASM’s agentless system allows swift and easy deployment of deceptions with minimal manpower required for both roll-out and daily operations. As soon as attackers attempt to use any form of deceptive information, Illusive detects and alerts enterprise security teams and integrates real-time, contextual forensic data directly into the incident record, enabling rapid and informed incident analysis and response.
“The combination of ASM’s ability to reduce the exposure of credentials in advance of attacks, with Illusive’s existing ability to plant convincing and realistic deceptions throughout an environment, will help organizations better prepare for attacks, and detect threat actors earlier in the attack lifecycle,” concluded Carmakal. “Illusive continues to innovate technology that helps organizations reduce their attack surface and mitigate the risk of data breaches.”
Illusive Networks is a pioneer of deception technology, empowering security teams to take informed action against advanced, targeted cyberattacks by detecting and disrupting lateral movement toward critical business assets early in the attack life cycle. Illusive’s Deceptions Everywhere® approach was conceived by cybersecurity experts with decades of combined experience in cyber warfare and cyber intelligence. With the ability to proactively intervene in the attack process, technology-dependent organizations can preempt significant operational disruption and business losses, and function with greater confidence in today’s complex, hyper-connected world.
1 Gartner, “Top 10 Strategic Technology Trends for 2018: Continuous Adaptive Risk and Trust,” David W. Cearley, Neil MacDonald, et al., 8 March 2018.
