Go Ahead, Get Paranoid: Rethinking Endpoint Security
In Dr. No, James Bond is about to leave his hotel room for some martinis (shaken, not stirred!) but he wants to make sure that no one peeks inside Her Majesty’s secret briefcase, which he leaves in the room. Being that it’s 1962, his best option is to sprinkle some fingerprint powder on the case’s metal latches. That way, he’ll be able to see if someone tried to open it. Cyber security managers should take note. Bond’s technique reveals an amazing affinity for endpoint protection, 50 years ahead of his time.
For Bond (Played by Sean Connery. Is there any other?), it doesn’t matter how his adversary gets into the hotel room, or into the country, for that matter. He could have flown in, taken a boat, a bus… It makes no difference what kind of lock picks or skeleton key he uses. All that matters is that Bond can detect that someone tried to get into the briefcase. That’s all he needs to know. Everything else is a meaningless distraction. This is the approach adopted by Nyotron, which is rethinking endpoint security.
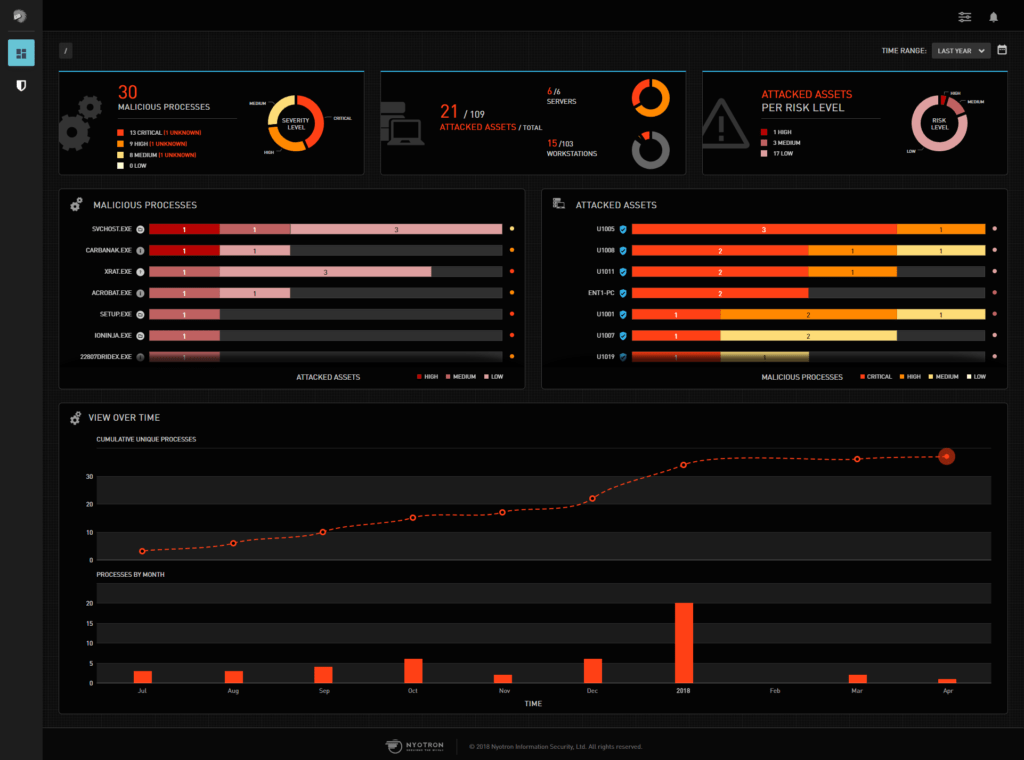
Nyotron Paranoid management console
Focus on Where the Damage is Being Done
Nyotron looked at the crowded, $1 billion endpoint protection space and came to the conclusion that many of the players were fighting an unwinnable battle against malware. Unlike James Bond, they were trying to catch the attacker while he was on the plane on his way to crack open the briefcase. They asked, in effect, why not just watch the briefcase?
“Sooner or later, the attacker needs to get to the endpoint, explained Gili Moller, Nyotron’s VP of Product and Marketing. For Nyotron, endpoints can be PCs, mobile devices or servers. “That’s where the data is. That’s where the attack target is operating. If you can steal or destroy data on the endpoint, or disrupt it, you’re succeeding as an attacker. That’s where we fight.”
Using software they named Paranoid, represented by the dauntless hedgehog mascot shown in the picture, Nyotron watches the endpoint’s operating system for signs of attack. The software automatically identifies legitimate OS behavior and rejects everything else. At the same time, it provides visibility. The company calls this EPR, for Endpoint Prevention and Response.
As Moller put it, “We know exactly what it looks like when a legitimate user takes an action like deleting a file. Right-clicking on a file and deleting is matched by a sequence of activities at the Kernel level. When a hacker tries to delete your file, it’s going to look totally different. If you know what to look for, the OS will tell you that something illegitimate is going on.” He added, “Paranoid can protect you against unknown threats, while giving you granular forensic visibility—including the attack timeline, origin and aim.”
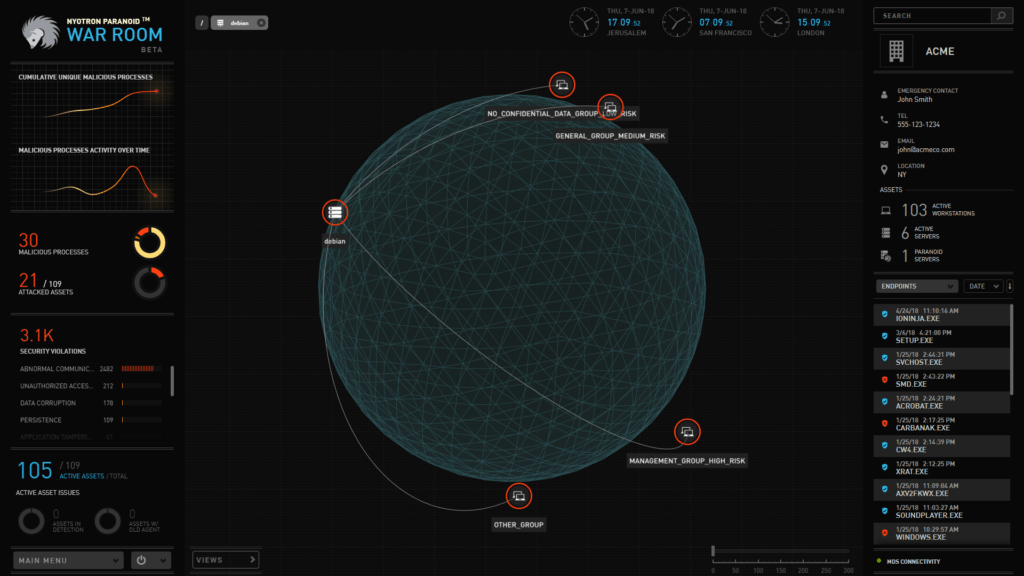
Nyotron Parnoid War Room
OS-Centric Security

Nyotron’s mascot is a hedgehog named Paranoid.
Nyotron calls this “OS-Centric Positive Security.” In independent testing by ICSA Labs, Paranoid was able to prevent 100% of threats, including Zero Day attacks, but yielded just 0.14% in false positives. “When we speak with potential clients, we hear about security analysts grinding up precious cycles investigating false positives. That’s a problem we are trying to solve.” The company’s clients include large healthcare providers and a major law enforcement agency.
Prevention is only one part of the Paranoid process. Nyotron integrates with SIEM systems and various incident response management tools. Paranoid generates alerts for SOC analysts. The company also maintains its own response center where it can monitor client’s environments if that service is requested.
