AI in Cybersecurity: Industry Perspectives
It is hard to miss the many references to the use of Artificial Intelligence (AI) in cybersecurity. Most, if not all security vendors now claim to utilize AI and Machine Learning (ML) in their solutions. This trend has provoked a fair amount of eye rolling. It’s the new thing. It’s the big thing. It’s a lie. It’s worthless, and so on.
There is surely a lot of hype and fud flying around about AI and ML in cybersecurity. That said, AI and ML form the basis for the only realistic countermeasures against highly sophisticated attackers. Human beings simply cannot keep up with the volume of analysis and pattern recognition required to defend digital assets today. What does it take to make AI and ML an effective part of cyber defense? Here are some selected perspectives on this important question.
Be Adaptive and Put It in Writing
According to Dr. Akli Adjaoute, Founder and CEO of Brighterion, an AI-driven cybersecurity vendor owned by MasterCard, adaptability is absolutely essential in AI for security. “Security changes every day,” he said. “Your countermeasures have to adapt. This means avoiding AI technologies based on pre-programmed rules—Meaning, don’t focus on learning from the past. I could teach a system to identify a cat, but would it recognize a cat from a different angle? That’s where you can become exposed to risk.”
“I could teach a system to identify a cat, but would it recognize a cat from a different angle? That’s where you can become exposed to risk.”
Brighterion puts this idea into action with their Smart Agents. Rather than working off of rules and trying to anticipate every possible threat scenario, the Smart Agents create profiles specific to each entity. As Adjaoute explained, the agents “behave according to their goals, observations, and the knowledge they continuously acquire through their interactions with other Smart Agents.” The figure shows the many layers of AI inputs each Smart Agent employs in its defense capability.
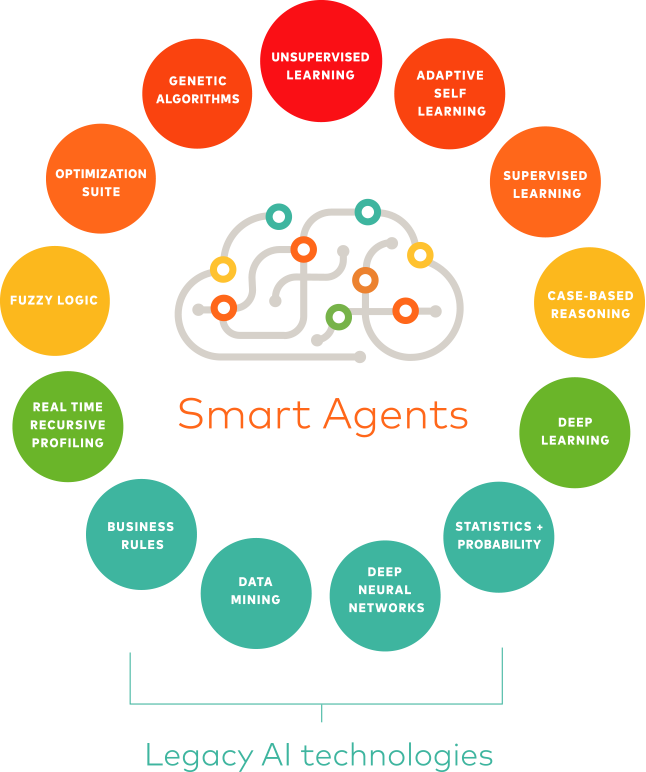 Adjaoute offered some further advice for organizations considering AI-driven security solutions. “Life is short,” he said. “Focus on what matters. Don’t waste time on digital assets that are not mission-critical.” In his experience, it’s also necessary to see a proof of value. “Whatever vendor you select, they should be able to demonstrate their specific value to you before you commit to them.” And, they should put their value in writing. “If an AI solution can really detect new threats, the vendor should put that in the contract. We do this. Any worthwhile AI vendor should be able to make that promise in writing. If they can’t, I would move on to the next supplier.”
Adjaoute offered some further advice for organizations considering AI-driven security solutions. “Life is short,” he said. “Focus on what matters. Don’t waste time on digital assets that are not mission-critical.” In his experience, it’s also necessary to see a proof of value. “Whatever vendor you select, they should be able to demonstrate their specific value to you before you commit to them.” And, they should put their value in writing. “If an AI solution can really detect new threats, the vendor should put that in the contract. We do this. Any worthwhile AI vendor should be able to make that promise in writing. If they can’t, I would move on to the next supplier.”
Work Across Multiple Tiers and Sectors
AI and ML work better with context and collaboration, as Oliver Wai, Vice President at IronNet Cybersecurity, revealed. IronNet’s product, Iron Defense, uses AI and ML to conduct network behavioral analytics. However, that process is just one element of IronNet’s broader approach to cyber security. “You can’t hide your behaviors on the network,” Wai shared. “That’s the building block of large schemes. However, to raise the level of defense, you have to share data across sectors and let multiple tiers of AI and ML make everyone that much smarter and well-protected.”
“You can’t hide your behaviors on the network,” Wai shared. “That’s the building block of large schemes.”
IronNet comes to this perspective with some pretty heavy credentials. The company was co-founded by Keith Alexander, a retired four-star Army general and former director of the National Security Agency. Yes, him… Alexander and his co-founders wanted to focus on addressing systemic flaws in security using ML. In their view, each sector needs situational awareness concerning other sectors. “The finance sector can benefit from knowing what threats the energy sector is fending off, and so forth,” Wai noted. IronNet enables ML-based pattern recognition to identity cross-sector threats.
The company facilitates threat sharing based on this approach. They also provide an anonymous rating system for assessments of incident response and alerting. “This helps build mutual trust, which is extremely important in making everyone more secure across multiple sectors,” Wai added.
Build off Category Knowledge
Generalization is one of the major complaints leveled at security vendors touting AI capabilities. Theoretically, any solution that can analyze data has at least some AI capabilities, however useless that might be. Specific experience counts, given the complexity and subtleties of cyber defense. For example, Aruba, which is owned by HPE, is leveraging its extensive experience in network traffic management in its approach to network security.
“Attackers are now able to evade perimeter defenses,” Lunetta explained. “We all know this, but the trick is to find them, which is not easy, because we typically don’t know what we’re looking for.”
As Larry Lunetta, VP of Marketing Security Solutions, put it, “We’ve been using AI to manage networks for years. Now, we’re applying all of that hard-won category knowledge to keeping the network secure.” He cited Aruba Introspect as the end result of this process. Introspect comprises User and Entity Behavior Analytics (UEBA) and Network Traffic Analysis (NTA) solutions. It uses AI-based machine learning and advanced analytics to detect otherwise hidden inside attacks.
“Attackers are now able to evade perimeter defenses,” Lunetta explained. “We all know this, but the trick is to find them, which is not easy, because we typically don’t know what we’re looking for. This is where AI is essential. With our experience in network management and traffic analysis, we can deploy Introspect to find what used to be invisible.”
Photo Credit: Medical Heritage Library, Inc. Flickr via Compfight cc
