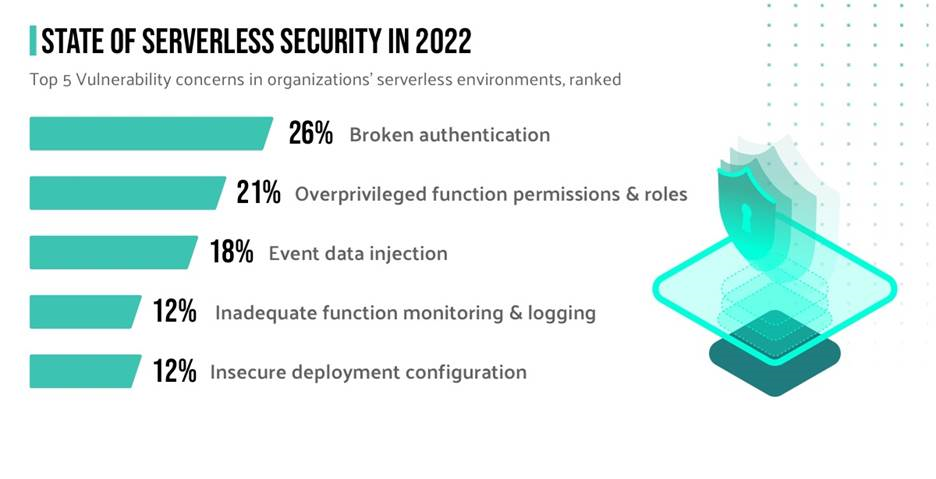
Serverless Security Vulnerabilities
Adoption of serverless is on the rise—nearly half (49%) of organizations are running their applications on the technology. While serverless technology eliminates many of the security responsibilities related to underlying technologies, developers are still on the hook regarding serverless functions.
For example, the particular transaction of a serverless function may be short-lived, but they have very broad access into other parts of your infrastructure—so the classic types of vulnerabilities seen in app server-based programs, including injection attacks, are all still possible in a serverless environment and are increasing.
According to the recent “State of #Serverless Security in 2022” report, 71 percent say their serverless applications have 10+ vulnerabilities on average, and 88% saw 4+ successful attacks on serverless applications in the past 12 months alone.
Below are the top five vulnerabilities, courtesy of Contrast Security’s State of Serverless Application Security Report: