RSA Profile: Trustonic
Trustonic deals with device security, an area of risk that needs attention now. It’s already a problem and it appears on its way to getting a lot worse if industry players don’t take the issue more seriously. Phones present one attack vector. Internet of Things (IoT) devices, which will soon outnumber phones, give attackers an even more attractive vehicle for fraud and malicious hacks.

Ben Cade, CEO of Trustonic
I spoke with Ben Cade, CEO of Trustonic, at RSA 2018. Ben’s background is well-suited to the challenge of securing devices. He founded Linaro the Open Source Software venture backed by IBM, Samsung, ARM and other key industry stakeholders. At ARM, he established and led the Security Division, grew their Infrastructure Business Unit and helped establish the ARM M&A and Corporate Venture Capital function.
Under Cade’s leadership, Trustonic now offers the Trustonic Secured Platforms (TSP™), a complete device security solution. TSP delivers a scalable set of services that enables a device Original Equipment Manufacturer (OEM) to meet their device security goals and to comply with industry mandates.
One of those mandates is the requirement to provide a Trusted Execution Environment (TEE) on each device. A TEE is a secure area of a main processor which guarantees code and data loaded inside are protected with respect to confidentiality and integrity.
TSP provides a TEE known as Kinibi®. It is essentially a secure operating system which enables Trusted Applications (TAs) to run on it. TSP is open, allowing device manufacturers to secure their apps while also giving the same level of protection to third-party app developers. Trustonic achieves this outcome with SDKs and open APIs.
“Extending trust to the device and the end user is one of the great security challenges of this era,” Cade said. “There’s potential for a lot of crime and mischief if the we all don’t get on top of this.” Trustonic gives app developers, device makers and any other relevant party, the ability to extend trust to an end user through a secure device. “With TSP, you can improve the user experience whilst providing better security, enabling simpler, richer and faster services to be deployed,” Cade added.
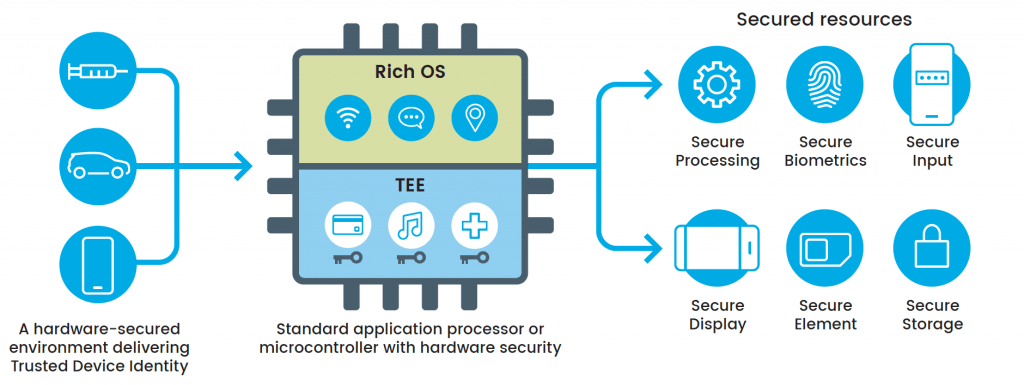
Trustonic TSP reference architecture
The TEE provided by Trustonic is secured by hardware, securing sensitive code execution and storage. It embeds each device with a Trusted Identity (a Root of Trust). This makes it possible for the identity of the device to be cryptographically proven and validated throughout its life. In addition, Trustonic facilitates the attestation of each device stage in a multi-step manufacturing process, providing protection against fraud in the supply chain through its Digital Holograms™.
