Using Policy to Foil the RATS in ICS
Xage Security just announced its new Policy Manager product, which can automatically enforce security policies

James Cagney, who hated “Dirty Rats”
across distributed critical infrastructure and Industrial Control Systems (ICSs). The news is another welcome drumbeat in the march toward a workable solution for the United States’ highly vulnerable power grid and oil and gas infrastructure. The announcement also aligns with new FERC regulations and legislation that will give the Department of Homeland Security more influence and responsibilities for ICS cyber security.
The threats against ICS and critical infrastructure are growing demonstrably worse, according to Duncan Greatwood, CEO of Xage. “Attacks are escalating,” he said. “The government is receiving a series of wakeup calls, and they’re not hitting the snooze button anymore.” Specifically, attackers are now taking advantage of Internet-connected devices at the edge of critical infrastructure networks. From such remote endpoints, malicious actors can inject a Remote Access Trojan (RAT).

Duncan Greatwood, CEO of Xage Security
A RAT can sit inside ICSs like SCADA systems and await remote activation, like Triton did in the attack on Schneider Electric in early 2018. They can spread laterally. Once active, RATS can disrupt systems, escalate privileges and steal information and generally wreak havoc on critical infrastructure. “RATs and the general problem of vulnerable endpoints makes the core of the ICS much less secure than it once was,” Greatwood added. “Historically, SCADA systems were insulated from most outside threats. Not true today.”
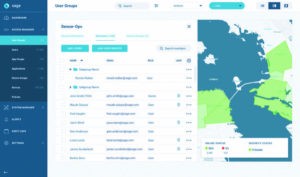
Screen shot of Xage Policy Manager
Xage Policy Manager offers power operators and other ICS owners an automated, decentralized security solution for distributed critical infrastructure. Policy Manager uses BlockChain to provide automatic, verifiable replication of security requirements across large numbers of devices, no matter how geographically dispersed they might be. For example, with Policy Manager, the ICS admin can set and enforce a rule to rotate complex passwords according to centrally defined timetables and policies. These features make Policy Manager useful for industrial companies that want to comply with government regulations as well.
Photo Credit: wwward0 Flickr via Compfight cc
