IT Security Policy for Multi-Cloud Environments
I spoke recently with Dr. Ratinder Paul Singh Ahuja, CEO of ShieldX, about the challenges of enforcing IT security policy in a multi-cloud environment. As a Sandbox Finalist at this year’s RSA conference, ShieldX has a solution for this potentially vexing problem.
Dr. Ahuja put this issue into context by comparing security practices in today’s cloud with those of the traditional on-premises data center. Consider the task of setting up a database on-premises. Before the cloud era, the database team might spend months determining its security policies, e.g. who could access it, will data be encrypted, does it require malware protection, what middleware will connect to it and so forth. “In the old world, this was fine because you know you would put things together for the next five years,” said Dr. Ahuja. “You would over-engineer stuff.” Those days are gone.

Dr. Ratinder Paul Singh Ahuja, CEO of ShieldX
The Potential Lack of IT Security Policy in Multi-Cloud
Today, as Dr. Ahuja pointed out, servers and databases are provisioned in the cloud on the fly. DevOps and cloud ops teams use Puppet and Chef along with other automation tools and templates to quickly roll out and modify applications. “What would have taken a month in the old world takes a day or less in the multi-cloud world,” he observed. And, he said, “There is no storage staffer or network ops person to talk to about security policy. In fact, the abstraction of the network dramatically shifts. You have virtualized concepts like software-defined networks.”
Indeed, in a multi-cloud environment, a database or application could be rolled out to Amazon (AWS) and Microsoft Azure while also being installed on VMware vSphere on-premises. Instances could get spun up and down quickly. Load volumes rise and fall with what Dr. Ahuja called “elastic demand.” These conditions are not well-suited for security through traditional “monolithic” network security appliances. It’s quite possible, in fact, for data assets deployed in a multi-cloud environment to be lacking in required security controls.
Compared to traditional on-premises infrastructure, multi-cloud expands the attack surface area. “All of a sudden, boundaries started dissolving,” said Dr. Ahuja. “This then gave rise to heightened awareness that if something gets into my multi-cloud environment and if I do not have sufficient controls inside those environments, then there will be unchecked lateral movement or something malicious walking towards a high value target.”
“I started ShieldX to try to solve this,” Dr. Ahuja said. “We fundamentally had to say, ‘Hey, what would security look like in a cloud environment?’ We had the chance to redefine the fundamental building blocks of security for a multi-cloud environment. In the old world, when we built boxes, we said, ‘What ASIC or chip would I need to give you the security?’ Now we’re saying, ‘If I’m going to build something for the cloud and I want to have a broad range of security controls that protect the cloud comprehensively, this is going to be elastic scaling from 0 to terabytes, all with an elastic pricing model in mind.”
Enforcing IT Security Policy in Multi-Cloud
The ShieldX approach to enforcing IT security policy in multi-cloud is to break the monolithic network security apparatus into microservices. The microservices can be deployed on demand. Software-defined, they are fast and agile for translating security policy definitions, such as encryption or packet inspection, into enforceable policy mechanisms wherever the data asset is deployed.
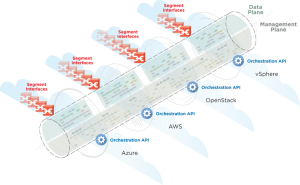
ShieldX reference architecture
ShieldX uses containerization and micro-services as the fundamental building blocks of what a security system does. It can apply micro-segmentation to the network, regardless of what cloud it’s running on. It’s a small footprint approach and allows for dynamic, elastic scaling where it’s needed. The solution also has automated discovery of cloud assets and an orchestration framework. With machine learning, the solution can define and enforce policies that represent the intentions of the system owners.
It’s still early in the life cycle for the security of software-defined networks in a multi-cloud environment. However, ShieldX provides an example of innovations in architecture can lead to solutions for enforcing IT security policy for assets deployed in the cloud.
