Cyber Security Policy Vs. Reality: The Xage Point of View on NERC CIP
Amidst all the talk of systemic vulnerability in America’s electrical grid, it’s not fair to accuse the industry of lacking coherent policy. The North American Electric Reliability Corporation (NERC) publishes an extensive cyber security policy framework for Critical Infrastructure Protection (CIP). The difficulty arises, however, with implementation. This is not a knock on smart, well-intentioned people who want to keep the power grid safe. It’s a matter of technology outrunning the reality of cyber security policy implementation.

Susanto Irwan, Co-Founder and VP of Engineering at Xage
I recently discussed the challenges of NERC CIP implementation with Susanto Irwan, whose company, Xage Security, is offering a novel approach to securing the Industrial Internet of Things (IIoT). The IIoT comprises the millions (soon to be billions) of industrial sensors and edge appliances that make the power grid and other industrial infrastructure function.
Addressing Gaps in Cyber Security Policy Enforcement
According to Irwan, one of the biggest gaps between NERC CIP policy and actual controls is user authentication. “Corporate identity and authentication systems live in the central data center,” Irwan explained. “They simply can’t scale to enable authentication for billions of devices located outside the data center, at the edge.” Thus, when NERC CIP calls for rotation of user credentials for IIoT devices in the power grid and revocation of credentials for users within 48 hours of employment termination, the reality is that these controls cannot be consistently enforced.
The solution, Irwan notes, is to decentralize the authentication process. This is what Xage (pronounced “zage”) does. Xage leverages Blockchain for autonomous, decentralized security for IIoT devices. “Earlier security approaches don’t do well with the intermittent connectivity and continuous adaptation of IIoT devices,” said Irwan. “We can no longer make the assumption that everything will be controlled by a static, continuously accessible and centralized infrastructure.”
The risks arising from this control gap are significant. Vulnerable to DDoS attacks and malware, IIoT devices in the power grid expose American society to potential chaos. Xage’s goal is to provide a workable risk mitigation technology for the IIoT as it affects the power grid and other vulnerable industrial networks.
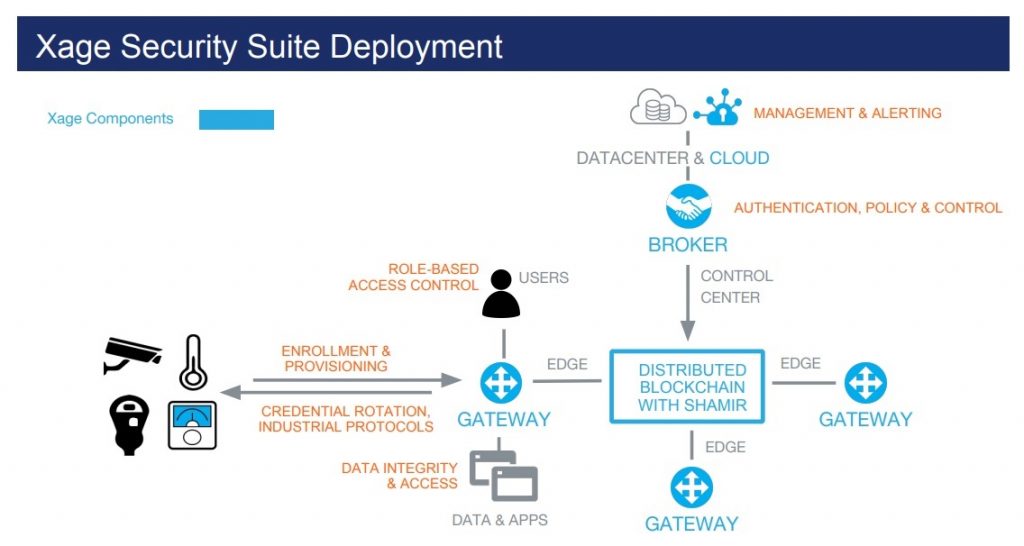
Xage reference architecture
Real Time Authentication
The Xage approach is to authenticate device users in real time, through a heterogeneous, distributed peer-to-peer process. With distributed credentials and real time authentication, utilities can be more confident that they are securing access to IIoT devices at the edges of their networks. They can realize the objective of control, rotating and revoking credentials as required. “We distribute trust at the edge, eliminating single-point-of-security-failure problems and enabling continuous edge operation” Irwan added. “This is the path utilities and other industrial concerns should follow to address today’s security challenges and to prepare for the inevitable growth of the IIoT to tens of billions of devices in the near future.”
